Table of Contents
Introduction to SSL
I believe that installing an SSL certificate for your website is incredibly important, especially if your website collects data from users. In today’s digital landscape, where online transactions are on the rise, ensuring internet security has become a top priority. It is crucial to protect sensitive information, such as credit card numbers, by transmitting them only to legitimate online businesses.
To maintain the privacy and security of customer information, it is essential for companies and organizations to add SSL certificates to their websites. By doing so, they create a secure environment for online transactions, giving customers peace of mind and confidence in the protection of their data.
A. Definition and Purpose of SSL
SSL (Secure Sockets Layer) is a crucial component in ensuring secure communication over the internet. It acts as a powerful cryptographic protocol that establishes an encrypted connection between a client, like a web browser, and a server, such as a website. By doing so, SSL guarantees that any sensitive data exchanged between them remains confidential and secure.
With SSL in place, users can browse websites with peace of mind, knowing that their personal information, passwords, and other sensitive data are protected from prying eyes. This encryption technology not only safeguards their privacy but also fosters trust and confidence in online interactions.
In today’s digital era, where data breaches and cyber threats are a concern, implementing SSL is an important step for any website or online business. It not only demonstrates a commitment to security but also enhances the overall user experience by providing a safe and reliable environment for online communication and transactions.
B. Importance of SSL in Securing Online Communications
SSL plays a vital role in securing online communications. With the increasing amount of sensitive information being transmitted over the internet, such as personal data, financial details, and login credentials, SSL provides the following benefits:
- Data Confidentiality: SSL encrypts data during transmission, preventing unauthorized parties from intercepting and reading it. This encryption ensures that only the intended recipient can decipher the information, keeping it safe from prying eyes.
- Authentication: SSL certificates validate the identity of a website, assuring users that they are communicating with a legitimate entity. This helps prevent phishing attacks and builds trust between the user and the website, enhancing the overall security of online transactions.
- Data Integrity: SSL includes mechanisms to verify the integrity of transmitted data. It ensures that the information remains unaltered during transit, detecting any unauthorized modifications or tampering attempts. This protects against data manipulation and ensures the integrity of the exchanged data.
- Trust and User Confidence: Websites using SSL display trust indicators, such as the padlock symbol and “https://” in the address bar. These indicators signal to users that the connection is secure, encouraging them to trust the website and proceed with their interactions. SSL helps build user confidence and establishes a secure online environment.
- Compliance with Security Standards: Many industries have specific security requirements and regulations that mandate the use of SSL to protect sensitive data. Adhering to these standards is essential for businesses to maintain compliance and safeguard user information.
In conclusion, SSL is a crucial component of secure online communication. It ensures data confidentiality, provides authentication, maintains data integrity, instills user trust, and helps businesses meet regulatory requirements. Implementing SSL is essential for protecting sensitive information and maintaining a secure online environment.
How SSL Works
A. Explanation of Asymmetric Encryption
SSL (Secure Sockets Layer) employs asymmetric encryption, also known as public-key cryptography, to establish a secure communication channel. Asymmetric encryption involves the use of two cryptographic keys: a public key and a private key.
- Public Key: The public key is widely distributed and accessible to anyone. It is used for encrypting data and verifying digital signatures. The public key can be freely shared with other parties without compromising the security of the communication.
- Private Key: The private key is kept secret and known only to the owner. It is used for decrypting data encrypted with the corresponding public key and for creating digital signatures. The private key must be securely stored and should never be shared with anyone else.
When a client and a server communicate, the server generates a key pair consisting of a public key and a private key. The server keeps the private key secure while distributing the public key to clients.
B. SSL Handshake Process
The SSL handshake is a crucial process that occurs at the beginning of a secure communication session. It establishes the encryption parameters and ensures the authenticity of the server. The SSL handshake process typically involves the following steps:
- Client Hello: The client initiates the handshake by sending a Client Hello message to the server. This message includes information about the SSL/TLS versions and cipher suites supported by the client.
- Server Hello: The server responds with a Server Hello message, selecting the highest SSL/TLS version and cipher suite that is supported by both the client and the server. The server also sends its digital certificate, which includes its public key.
- Certificate Verification: The client verifies the authenticity of the server’s digital certificate. It checks the certificate’s validity, the issuing Certificate Authority (CA), and whether the certificate has been revoked. The client may also verify that the server’s domain name matches the one in the certificate.
- Key Exchange: If the server’s certificate is deemed valid, the client generates a random session key. The session key is encrypted with the server’s public key and sent back to the server.
- Server Key Exchange: In some cases, the server may send additional information, such as its own certificate or the Diffie-Hellman parameters for key exchange.
- Session Key Generation: Both the client and the server use the exchanged keys to independently generate a shared session key. This session key is used for symmetric encryption and decryption during the remainder of the SSL session.
- Cipher Suite Confirmation: The client sends a message to the server, indicating the cipher suite and session key it has chosen. The server acknowledges the selected cipher suite, and both client and server begin encrypted communication using the agreed-upon parameters.
C. SSL Certificates and Their Role in Encryption
SSL certificates play a crucial role in establishing the authenticity and trustworthiness of a website or server. These digital certificates are issued by Certificate Authorities (CAs) and contain information about the website’s identity and public key.
When a client connects to a server, it checks the server’s digital certificate to verify its authenticity. The client ensures that the certificate is issued by a trusted CA and that the certificate’s details match the domain name of the server. The public key in the certificate is used for encrypting the session key during the SSL handshake.
D. SSL/TLS Protocols and Their Evolution
SSL has evolved into the more secure Transport Layer Security (TLS) protocol, although the terms SSL and TLS are often used interchangeably. Over the years, several versions of SSL/TLS have been developed to address security vulnerabilities and improve encryption strength.
The major versions of SSL/TLS are:
- SSL 2.0: Introduced in the 1990s, SSL 2.0 was the first widely used version of SSL. However, it had several security flaws and vulnerabilities, leading to its deprecation and discontinuation.
- SSL 3.0: Released in 1996, SSL 3.0 addressed some of the security weaknesses of SSL 2.0. It introduced the SSL handshake process, which established secure connections through key exchange and cipher negotiation. However, SSL 3.0 was also found to have significant security vulnerabilities, such as the POODLE (Padding Oracle On Downgraded Legacy Encryption) attack, which led to its deprecation.
- TLS 1.0: Released in 1999 as an upgrade to SSL, TLS 1.0 aimed to provide better security and address the vulnerabilities present in SSL 3.0. TLS 1.0 introduced several cryptographic improvements and cipher suites. Despite its improvements, TLS 1.0 still had some security weaknesses, such as vulnerabilities to attacks like BEAST (Browser Exploit Against SSL/TLS).
- TLS 1.1: Released in 2006, TLS 1.1 further enhanced the security of TLS 1.0. It addressed vulnerabilities and introduced new cryptographic algorithms and hash functions. TLS 1.1 provided better protection against known attacks, improving the overall security of SSL/TLS communication.
- TLS 1.2: Released in 2008, TLS 1.2 is the most widely adopted and currently recommended version of TLS. It introduced stronger cryptographic algorithms, enhanced security features, and improved resistance to attacks. TLS 1.2 has become the standard for secure communication, offering robust encryption and authentication mechanisms.
- TLS 1.3: Released in 2018, TLS 1.3 is the latest version of the TLS protocol. It focuses on improving security, performance, and privacy. TLS 1.3 streamlines the handshake process, reduces latency, and removes outdated cryptographic algorithms. It also provides stronger encryption and forwards secrecy by default. TLS 1.3 is designed to offer better protection against attacks and enhance overall SSL/TLS security.
As technology advances and new security threats emerge, it is essential to keep SSL/TLS protocols up to date. Implementing the latest supported version of TLS is crucial to ensure the highest level of security in online communications. Additionally, staying informed about any vulnerabilities or weaknesses in SSL/TLS implementations and promptly applying patches or updates is essential for maintaining a secure environment.
SSL Certificates
A. Overview of SSL Certificate Authorities (CAs)
SSL certificates are issued by Certificate Authorities (CAs), trusted entities that verify the identity and authenticity of websites. CAs play a crucial role in establishing trust and ensuring the security of SSL/TLS communication. Here’s an overview of CAs and their responsibilities:
- Verification: CAs verify the ownership and control of the domain for which an SSL certificate is being requested. They validate the information provided by the certificate applicant to ensure it matches the domain’s ownership details.
- Certificate Issuance: Once the verification process is complete, the CA issues the SSL certificate. The certificate contains the domain name, the public key of the server, and other relevant details.
- Trustworthiness: CAs are trusted third-party entities that are included in web browsers and operating systems. The inclusion of CAs in trusted root stores allows browsers to verify the authenticity and validity of SSL certificates issued by them.
B. Different Types of SSL Certificates (DV, OV, EV)

There are different types of SSL certificates available, each providing a different level of validation and security. The main types of SSL certificates are:
- Domain Validated (DV) Certificates: DV certificates are the most basic type of SSL certificate. They require a simple verification process where the CA verifies the domain ownership. DV certificates are issued quickly and are suitable for basic encryption needs.
- Organization Validated (OV) Certificates: OV certificates require a more rigorous verification process. In addition to domain ownership, the CA verifies the organization’s details, including its legal existence and physical address. OV certificates provide a higher level of trust and authentication compared to DV certificates.
- Extended Validation (EV) Certificates: EV certificates offer the highest level of validation and trust. The verification process for EV certificates is the most stringent, including a thorough examination of the organization’s legal and physical existence. EV certificates display the organization’s name prominently in the browser’s address bar, signaling a high level of security and trust to users.
C. Certificate Signing Process and Certificate Chain
The certificate signing process involves several steps:
- Certificate Signing Request (CSR): The certificate applicant generates a CSR, which includes the public key and relevant information about the domain and organization.
- CSR Submission: The applicant submits the CSR to the CA, along with any necessary documentation for verification.
- Verification and Issuance: The CA verifies the information provided in the CSR and conducts the necessary checks based on the certificate type. Once the verification is successful, the CA issues the SSL certificate.
- Certificate Chain: SSL certificates are issued in a hierarchical structure called a certificate chain. The chain includes the SSL certificate issued for the domain as well as intermediate and root certificates. The root certificate is the highest level of authority and is pre-installed in browsers and operating systems.
D. Validity and Expiration of SSL Certificates
SSL certificates have a specific validity period, after which they expire and must be renewed. The validity period can vary, typically ranging from one to three years. Certificate authorities provide options for different validity periods during the certificate issuance process.
Expiration dates are crucial because an expired certificate can lead to security warnings and disruptions in SSL/TLS communication. It is essential to monitor certificate expiration dates and renew them before they expire to maintain uninterrupted security.
Renewal processes may involve generating a new CSR, undergoing verification again, and obtaining a new SSL certificate from the CA. Many organizations utilize certificate management tools and automated processes to track and renew certificates in a timely manner, ensuring continuous security and compliance.
Regularly updating and renewing SSL certificates is necessary to maintain
the security and trustworthiness of websites. Failure to renew SSL certificates can result in security warnings for users and potential disruptions in website functionality.
It is important to keep track of SSL certificate expiration dates and establish a process for timely renewal. This can be done manually or through the use of certificate management tools that provide notifications and automated renewal options. By staying proactive and ensuring certificates are renewed before they expire, website owners can maintain a secure and uninterrupted online presence.
Furthermore, it’s worth noting that some CAs offer revocation services for SSL certificates. Certificate revocation may be necessary if a certificate is compromised, the private key is lost, or the certificate information becomes outdated or invalid. Revoked certificates are added to Certificate Revocation Lists (CRLs) or Certificate Authority Revocation Lists (CARLs), which browsers and systems can check to verify the validity of a certificate.
In conclusion, SSL certificates have a specific validity period and must be renewed before they expire to maintain the security and trustworthiness of websites. Monitoring expiration dates, establishing renewal processes, and considering certificate revocation when necessary are all important aspects of SSL certificate management. By ensuring up-to-date and properly maintained SSL certificates, website owners can provide a secure online experience for their users.
Benefits of SSL
A. Data Confidentiality and Encryption
One of the primary benefits of SSL is the encryption it provides for data transmitted between a client and a server. SSL uses robust encryption algorithms to scramble the data, making it unreadable to anyone who intercepts it illegitimately. This encryption ensures that sensitive information such as passwords, credit card numbers, and personal details remain confidential and protected from unauthorized access.
B. Authentication and Trustworthiness
SSL certificates play a crucial role in establishing trust and authenticity. When a website has an SSL certificate, it undergoes a verification process that confirms its identity and ownership. This verification is performed by a trusted Certificate Authority (CA), which vouches for the website’s legitimacy. When users see the padlock icon or the “https” prefix in the website’s URL, it provides them with confidence that the website is genuine and secure.
C. Protection against Phishing and Man-in-the-Middle Attacks
SSL helps protect against phishing attacks, where malicious actors attempt to deceive users by impersonating legitimate websites. With SSL, users can verify the authenticity of a website by checking its SSL certificate. This reduces the risk of falling victim to phishing scams.
SSL also safeguards against man-in-the-middle attacks, where an attacker intercepts communication between a client and a server to gain unauthorized access or alter the transmitted data. SSL encryption ensures that the data exchanged between the client and server remains confidential and integral, making it difficult for attackers to eavesdrop or manipulate the information.
D. Enhanced Search Engine Ranking and Customer Trust
SSL has become an important factor in search engine optimization (SEO). Major search engines, such as Google, consider SSL as a ranking signal, giving preference to websites that have implemented SSL. Having an SSL certificate can positively impact a website’s search engine ranking, potentially leading to increased visibility and organic traffic.
Furthermore, SSL helps build trust with customers. In an era where online privacy and security are significant concerns, displaying the padlock icon and “https” in the URL reassures users that their data is secure when interacting with a website. This enhanced trust can lead to higher customer confidence, increased conversions, and improved customer loyalty.
In summary, SSL offers several benefits, including data confidentiality, authentication, protection against phishing and man-in-the-middle attacks, improved search engine ranking, and enhanced customer trust. Implementing SSL is essential for securing online communications and establishing credibility in today’s digital landscape.
SSL Implementation
A. SSL for Websites and Web Applications
- Installing an SSL Certificate on a Web Server: To implement SSL for a website or web application, you need to obtain an SSL certificate from a trusted Certificate Authority (CA). The process typically involves generating a Certificate Signing Request (CSR), submitting it to the CA, and following their instructions for certificate issuance. Once you receive the SSL certificate, you can install it on your web server. This may involve configuring the server software (e.g., Apache, Nginx, Microsoft IIS) to enable SSL/TLS and specifying the location of the SSL certificate files.
- Enforcing HTTPS for Secure Browsing: After installing the SSL certificate, it’s important to enforce HTTPS (HTTP over SSL/TLS) for secure browsing. This can be achieved by configuring your web server to redirect all HTTP requests to their HTTPS counterparts. By doing this, any communication between the client and the server is automatically encrypted, ensuring that sensitive information remains protected.
- Common SSL Configuration Issues and Troubleshooting: Implementing SSL can sometimes come with configuration challenges. Common issues include certificate mismatches, incorrect server configurations, and mixed content warnings. It’s crucial to ensure that the SSL certificate is properly installed, the server is correctly configured, and all resources (e.g., images, scripts) are loaded securely via HTTPS. Troubleshooting techniques may involve checking server logs, examining browser error messages, and utilizing SSL testing tools.
B. SSL for Email Communication
- Securing Email Servers with SSL/TLSSSL/TLS can be utilized to secure email communication between servers. Email servers, such as SMTP (Simple Mail Transfer Protocol) servers, can be configured to use SSL/TLS encryption for incoming and outgoing email traffic. This involves obtaining an SSL certificate for the email server, configuring the server software (e.g., Postfix, Exchange) to enable SSL/TLS, and specifying the appropriate SSL settings.
- Using SSL for Email Clients (e.g., Outlook, Thunderbird): Email clients can also benefit from SSL/TLS encryption. Most modern email clients support SSL/TLS for secure communication with email servers. Users can configure their email client software (e.g., Outlook, Thunderbird) to use SSL/TLS when connecting to email servers. This ensures that emails are encrypted during transmission, protecting their confidentiality.
C. SSL for Other Protocols (FTP, VPN, etc.)
- SSL/TLS in File Transfer Protocols: Secure File Transfer Protocol (SFTP) and FTPS (FTP over SSL/TLS) are secure alternatives to traditional FTP. These protocols use SSL/TLS encryption to protect file transfers between clients and servers. Implementing SSL/TLS for file transfer protocols involves obtaining an SSL certificate, configuring the FTP server to enable SSL/TLS, and configuring client applications to use SSL/TLS for secure file transfers.
- SSL in Virtual Private Networks (VPNs): SSL/TLS can be utilized in Virtual Private Networks (VPNs) to establish secure connections between clients and VPN servers. This ensures that data transmitted between the client and the VPN server is encrypted and protected. SSL-based VPNs use SSL/TLS protocols for authentication, encryption, and integrity checks, providing a secure remote access solution.
Implementing SSL for various protocols requires obtaining SSL certificates, configuring server software, and ensuring that client applications are set up to use SSL/TLS for secure communication.
Note: It’s important to regularly update SSL certificates, keep track of their expiration dates, and stay informed about security best practices to maintain a secure SSL implementation.
SSL Vulnerabilities and Mitigation
A. Overview of Common SSL Vulnerabilities
SSL has faced several vulnerabilities over the years. It’s important to be aware of these vulnerabilities and understand how to mitigate them. Here are a few notable examples:
- POODLE (Padding Oracle On Downgraded Legacy Encryption): This vulnerability affected SSL 3.0 and allowed attackers to exploit the protocol’s padding mechanism to decrypt information. It highlighted the need to discontinue the use of SSL 3.0 and transition to more secure protocols like TLS.
- Heartbleed: Heartbleed was a critical vulnerability in the OpenSSL library that allowed attackers to retrieve sensitive information from the memory of servers. It emphasized the importance of promptly updating SSL libraries to the latest patched versions.
B. Best Practices for SSL Implementation and Configuration
To mitigate SSL vulnerabilities and ensure a secure implementation, follow these best practices:
- Strong Encryption and Key Exchange: Use modern cryptographic algorithms and key exchange mechanisms that provide robust encryption and authentication, such as AES (Advanced Encryption Standard) and Elliptic Curve Cryptography (ECC).
- Enable Perfect Forward Secrecy (PFS): Implement Perfect Forward Secrecy, which ensures that even if the server’s private key is compromised in the future, previously encrypted communications remain secure.
- Use Strong Certificate Key Lengths: Ensure that SSL certificates use strong key lengths, such as 2048 bits or higher, to withstand potential attacks on cryptographic keys.
- Disable Weak Cipher Suites: Disable weak or outdated cipher suites that may be vulnerable to attacks. Only allow the use of secure cipher suites with strong encryption algorithms.
- Implement Strict Certificate Validation: Configure servers and clients to perform strict certificate validation, including checking for valid certificate chains, expiration dates, and revocation status.
C. Keeping SSL Libraries and Software Up to Date
Regularly update SSL libraries, web server software, and other components involved in SSL/TLS communication. Stay informed about security advisories and promptly apply security patches and updates. Outdated software may have known vulnerabilities that attackers can exploit.
D. SSL/TLS Hardening Techniques and Recommendations
Implement SSL/TLS hardening techniques to enhance the security of your SSL implementation:
- Disable Insecure Protocols and Features: Disable outdated and insecure protocols, such as SSL 2.0 and SSL 3.0, and deprecated features like weak cipher suites and insecure renegotiation.
- Use HSTS (HTTP Strict Transport Security): Enable HSTS to ensure that clients always connect to your website using HTTPS, even if they type “http://” in the URL.
- Implement OCSP Stapling: OCSP Stapling reduces reliance on Certificate Authorities’ OCSP servers by having the server include a signed OCSP response with the certificate during the SSL handshake.
- Enable Security Headers: Implement security headers like Content Security Policy (CSP), X-Frame-Options, and X-XSS-Protection to protect against cross-site scripting (XSS), clickjacking, and other web-based attacks.
- Regularly Perform Security Audits: Conduct regular security audits and vulnerability scans to identify and address any potential SSL-related security weaknesses.
By following best practices, keeping SSL software up to date, and implementing SSL/TLS hardening techniques, you can minimize the risk of SSL vulnerabilities and maintain a secure SSL environment.
SSL Certificates and Extended Validation (EV)
A. Explanation of EV Certificates and Their Additional Validation Steps
Extended Validation (EV) certificates are a type of SSL certificate that provides the highest level of validation and trust. They undergo a more rigorous verification process compared to other types of SSL certificates. The additional validation steps for EV certificates typically include:
- Verification of Legal Existence: The Certificate Authority (CA) validates the legal existence of the entity behind the website. This involves verifying the organization’s registration and ensuring it is in good standing.
- Verification of Physical Address: The CA verifies the organization’s physical address by cross-checking it with trusted third-party databases, such as government records or commercial databases.
- Verification of Identity: The CA verifies the identity of the organization’s representative who is requesting the EV certificate. This may involve checking the individual’s identity documents, such as passports or driver’s licenses.
The additional validation steps of EV certificates help establish a higher level of trust and assurance for website visitors.
B. Visual Indicators of EV Certificates in Browsers
Browsers display visual indicators to differentiate EV certificates from other types of SSL certificates. These indicators provide users with a visual cue of the enhanced trust associated with EV certificates. Common visual indicators of EV certificates include:
- Green Address Bar: In most browsers, EV certificates trigger the display of a distinctive green address bar, prominently indicating the website’s identity and security. The organization’s name may be displayed in the green address bar, providing users with immediate visual assurance.
- Company Name: Browsers may display the verified organization’s name alongside the padlock icon or in the certificate details section. This reinforces the legitimacy and trustworthiness of the website.
The prominent visual indicators associated with EV certificates help users identify trustworthy websites and provide an additional layer of confidence during online interactions.
C. Benefits of EV Certificates for E-commerce and Online Transactions
EV certificates offer several benefits, particularly for e-commerce and online transactions:
- Enhanced Trust and Confidence: The rigorous validation process of EV certificates builds trust and confidence in the organization and its website. This is especially crucial for e-commerce websites handling sensitive customer information, such as credit card details.
- Improved Conversion Rates: The visual indicators associated with EV certificates, such as the green address bar, help instill confidence in users. Studies have shown that the presence of EV certificates can positively impact conversion rates by reassuring customers about the legitimacy and security of the website.
- Protection Against Phishing Attacks: EV certificates provide stronger protection against phishing attacks. The clear visual indicators make it more difficult for attackers to impersonate legitimate websites, as users are trained to look for the green address bar as a trust indicator.
- Compliance with Industry Standards: Certain industries, such as finance and healthcare, have regulatory requirements for securing online transactions. EV certificates can help meet these compliance requirements by demonstrating a commitment to strong security practices.
- Brand Reputation and Differentiation: Displaying the organization’s name in the browser’s UI through an EV certificate can enhance brand reputation and differentiate the website from competitors. It signals a commitment to security and professionalism.
Overall, EV certificates provide an additional layer of trust, visibility, and assurance for websites engaged in e-commerce and online transactions. They offer tangible benefits in terms of customer confidence, conversion rates, protection against phishing, and compliance with industry standards.
Why SSL is important to Nigerian Businesses that own websites
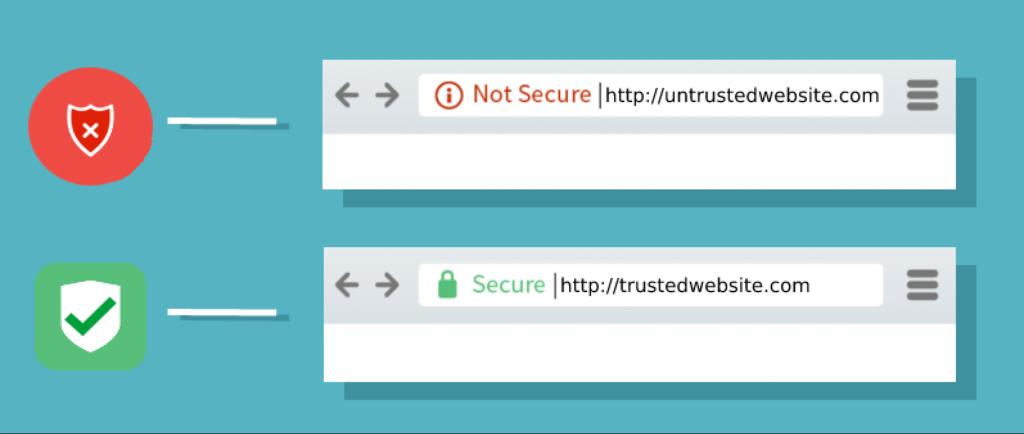
Nigerian businesses that own websites need to prioritize the implementation of SSL certificates and HTTPS for their online platforms. This is crucial for several reasons:
- Data Security: Implementing SSL certificates and enabling HTTPS ensures the encryption of data transmitted between the website and its visitors. It safeguards sensitive information, such as customer details, login credentials, and financial transactions, from unauthorized access or interception by malicious actors. This helps protect the privacy and integrity of customer data, which is essential for building trust and maintaining a positive reputation.
- Customer Trust: With the increasing awareness of online security risks, customers have become more cautious about sharing their personal information. By having SSL certificates and HTTPS, Nigerian businesses can visibly demonstrate their commitment to data protection and customer security. This helps establish trust and confidence among users, leading to increased customer loyalty and higher conversion rates.
- Regulatory Compliance: Nigerian businesses operating in various industries, such as finance, healthcare, and e-commerce, are subject to data protection regulations and compliance requirements. Implementing SSL certificates and HTTPS is often a prerequisite for meeting these regulatory standards. By ensuring compliance, businesses can avoid penalties, legal issues, and reputational damage.
- Enhanced Search Engine Ranking: Search engines, including Google, consider SSL as a ranking factor in their algorithms. Websites with SSL certificates and HTTPS tend to rank higher in search engine results, leading to increased visibility and organic traffic. By implementing SSL, Nigerian businesses can improve their online presence and attract more potential customers.
- Protection against Phishing Attacks: Phishing attacks, where malicious entities attempt to deceive users by impersonating legitimate websites, are a significant concern in the online landscape. SSL certificates help protect against such attacks by providing visual indicators (such as the padlock icon and “https” in the URL) that signal the authenticity and security of the website. Nigerian businesses can safeguard their customers from falling victim to phishing scams and prevent potential financial losses.
In summary, Nigerian businesses that own websites should prioritize the implementation of SSL certificates and HTTPS. It ensures data security, builds customer trust, aids regulatory compliance, improves search engine ranking, and protects against phishing attacks. By taking these necessary steps, Nigerian businesses can create a secure online environment, foster customer loyalty, and drive business growth in the digital landscape.
Steps to get SSL and install it on a website
- Determine Your SSL Certificate Needs:
- Identify the type of SSL certificate that suits your website’s requirements. This can include options like Domain Validation (DV), Organization Validation (OV), or Extended Validation (EV) certificates.
- Consider the number of domains and subdomains you need to secure. Some SSL certificates cover a single domain, while others include multiple domains or wildcard options.
- Choose a Certificate Authority (CA):
- Research and select a reputable Certificate Authority that offers SSL certificates. Some popular CAs include Let’s Encrypt, DigiCert, Comodo, and GlobalSign.
- Compare pricing, certificate features, customer support, and the CA’s reputation.
- Generate a Certificate Signing Request (CSR):
- Generate a CSR from your web server or hosting control panel. This process may vary depending on the server software you’re using (e.g., Apache, Nginx, Microsoft IIS).
- The CSR contains information about your organization, such as your domain name, company name, location, and public key.
- Submit the CSR and Complete the Verification Process:
- Provide the CSR to the CA during the SSL certificate purchase process.
- The CA will initiate the validation process to verify your organization’s information, ownership of the domain, and other details.
- Follow the CA’s instructions to complete the verification, which may involve email verification, phone calls, or submitting legal documents.
- Receive and Install the SSL Certificate:
- Once the verification is complete, the CA will issue your SSL certificate.
- Download the SSL certificate files provided by the CA. These typically include the certificate file, intermediate certificate(s), and possibly a private key file.
- Upload the certificate files to your web server or hosting provider’s control panel.
- Configure your web server software to enable SSL/TLS and specify the location of the SSL certificate files. This process varies depending on the server software you’re using.
- Test and Verify SSL Installation:
- Test your SSL installation using online SSL checkers or SSL validation tools.
- Ensure that your website is accessible over HTTPS and that the SSL certificate is correctly installed and valid.
- Check for any mixed content warnings, which indicate that some resources are being loaded over HTTP instead of HTTPS.
- Update Your Website’s Links and Settings:
- Update any hardcoded links within your website’s code, templates, or content to use HTTPS instead of HTTP.
- Update any website settings or configuration files to enforce HTTPS, such as redirecting all HTTP requests to their HTTPS counterparts.
- Monitor SSL Certificate Expiry and Renewal:
- Keep track of the SSL certificate’s expiration date and plan for its renewal well in advance.
- Set up reminders or notifications to ensure timely renewal of the SSL certificate.
It’s worth mentioning that the process and instructions for installing an SSL certificate may vary depending on factors such as your web server software, hosting provider, and the chosen certificate authority (CA). To ensure a smooth installation tailored to your specific setup, I highly recommend consulting the documentation and support resources offered by your web server, hosting provider, and the CA you have selected.
By referring to these valuable resources, you can access detailed and accurate instructions that are specifically designed to meet the requirements of your unique configuration. Following the guidelines provided by your trusted sources will not only streamline the installation process but also ensure that you have a reliable and secure SSL certificate implementation.
Remember, seeking assistance and guidance from the experts in your web server software, hosting provider, and CA will empower you to make informed decisions and navigate the installation process with confidence.


